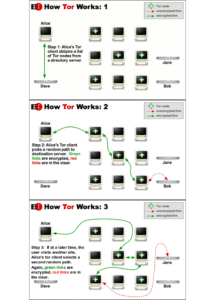
Welcome to this week’s Tip of the Hat! This week marks two important dates. The first date is this Tuesday! Data Privacy Day is a worldwide event to raise awareness as well as promote data privacy practices. Some last-minute ideas to celebrate #DataPrivacyDay at your library can include:
- Posts to your library’s blogs, news feed, or social media about how patrons can protect their privacy online and at the library. Not sure what to share with your patrons? The User Tools section on the Choose Privacy Everyday is a good place to start.
- If you need a last-minute book/material display for your library, here is a list of materials from the Library Freedom Institute to help you seed your public display.
- Cookies for your staff – with a catch, of course. If your library has a staff room or area, bring in some cookies to share and place some information about web trackers and cookies alongside the actual cookies.
- Consider distributing How Did We Get Here?: A Zine About Privacy at the Library at your library, and have a brown bag lunch (or better yet, provide lunch) discussion about privacy practices at the library.
- If you work with students, or if you have a student in your household (or if you’re a student yourself!), read up on students and privacy at https://studentprivacy.ed.gov/.
The second date marks the first anniversary of LDH Consulting Services! We launched at Midwinter 2019, aiming to provide libraries and library vendors guidance on all things library data privacy. It’s been a busy year getting the word out at our first ALA Annual, as well as word of mouth and this newsletter. This first year saw many training sessions, legislation reviews, and even a guest lecture or two! Thank you to everyone – our clients, supporters, newsletter subscribers – for helping LDH through the first year. We hope to serve the library and vendor community in protecting patron privacy for years to come.
Speaking of serving – LDH is still accepting projects and clients for Summer and Fall of 2020. We have a variety of training offerings for staff, including data lifecycle management, vendors and privacy, privacy impact assessments, and implementing privacy at your organization. LDH can also help you keep track of developing data privacy regulations in your state! With California’s new data privacy law in effect, many other states are looking to implement similar laws that can impact how libraries do business with vendors concerning patron privacy. If your organization needs that initial push in adopting best privacy practices or a review of existing privacy policies and practices, LDH is more than ready to help with that push.
The majority of our clients come to LDH through word of mouth, so we appreciate you all telling your colleagues about LDH and our services!