Academic libraries have been in the information security spotlight due to the resurgence of Silent Librarian. The collection of academic user accounts gives attackers access to whatever the user has access to in the campus network, including personal data. Attackers gaining access to library patron data was not the reason why academic library information security was in the news again this past month, however.
Protecting The Bottom Line
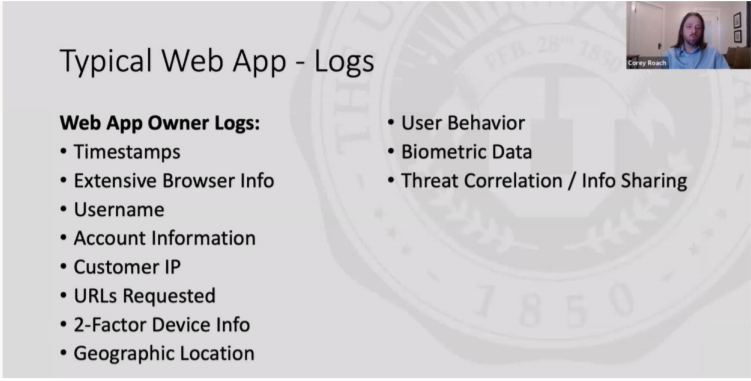
In late October, the Scholarly Networks Security Initiative (SNSI) presented a webinar [slides, transcript] that made several controversial statements and proposals. The one that caught the attention of the academic researcher and library worlds is the proposal of a publisher proxy tool to monitor user access and use of publisher resources. In the transcript and slides, the proposal included tracking behavioral data in addition to other personally identifiable data. For example, the publisher would actively track the subjects of the articles that the user is searching and reading:
159
00:29:10.020 –> 00:29:17.280
Corey Roach: You can also move over to behavioral stuff. So it could be, you know, why is a pharmacy major suddenly looking up a lot of material on astrophysics or
160
00:29:18.300 –> 00:29:27.000
Corey Roach: Why is a medical professional and a hospital suddenly interested in internal combustion things that just don’t line up and we can identify fishy behavior.
While there are other points of contention in the presentation (we recommend reading the transcript and the slides, as well as the articles linked above), the publisher proxy tool brings up a perennial concern around information security practices that libraries need to be aware of when working with IT and publishers.
You Say Security, But What About Privacy?
Security and privacy are not one-to-one equivalents. We covered the differences in security and privacy in a previous post. Privacy focuses on the collection and processing of personal data while security focuses on protecting organizational assets that may include personal data. Privacy is impossible without security. Privacy relies on security to control access and use of personal data. However, there is the misconception that security guarantees privacy. Security is “do one thing and do it well” – protect whatever it’s told to protect. Security does not deal with the “why” in data collection and processing. It does the job, no questions asked.
When security measures like the proxy tool above are touted to protect publisher assets, the question of “why this data collection and tracking” gets lost in the conversation. Libraries, in part, also collect behavioral data through their proxies to control access to library resources. Even though this data collection by libraries is problematic in itself, the fact remains that the data in this proxy is collected by the library and is subject to library policy and legal regulations around library patron data. The same information collected by a vendor tool may not be subject to the same policies and regulations – outside of California and Missouri, there are no state laws specifically regulating vendor collection, processing, and disclosure of library patron data. Therefore, any data collected by the vendors are only subject to whatever was negotiated in the contract and the vendor privacy policies, both of which most likely allow for extensive collection, processing, and disclosure of patron data. Security that uses patron data doesn’t necessarily guarantee patron privacy and could even put patron privacy in jeopardy.
Bringing Privacy into Library InfoSec
Academic libraries are part of a campus system and are one of many ways an attacker can gain access to campus assets, including personal data, as demonstrated by Silent Librarian. However, academic libraries are also targets for increased surveillance in the name of information security, as illustrated by the SNSI presentation. The narrative of “academic library as the weak link in a campus network” can force libraries into a situation where patron privacy and professional ethics are both compromised. This is particularly true if this narrative is driven by information security professionals not well acquainted with privacy and data ethics or by vendors who might financially benefit from the data collected by this increased surveillance of library patrons.
Library organizations and groups are weighing in on how information security should consider library privacy and data ethics. This Tuesday, ALA will be hosting a Town Hall meeting about surveillance in academic libraries. DLF’s Privacy and Ethics in Technology Working Group and the Library Freedom Project, co-collaborators with ALA’s Town Hall event, will most likely add to the conversation in the coming weeks with resources and statements. We’ll keep you updated as the conversation continues!
In the meantime…
A small postscript to the blog post – one reoccurring theme that we come across when talking to libraries about privacy is the importance of relationships with others in and outside the library. These relationships are key in creating buy-in for privacy practices as well as creating strong privacy advocates in the organization. What type of relationship do you have with your organizational information security folks? Check out this short presentation about building organizational relationships to promote a strong privacy and security culture if you are still wondering where to start.



