Welcome to this week’s Tip of the Hat!
A new year brings New Year resolutions. If you resolved to adopt better privacy practices and tools, you’re in luck! This week’s newsletter continues our exploration of the Privacy Tech Toolkit with the Tor browser and network.
Tor Basics
Tor enables users to anonymously browse and communicate online through two main parts. The first part is the Tor network, a worldwide network of servers. These servers serve as relays, sending encrypted information to randomly selected relays, masking the location of the user of the network. “Tor” stands for “the onion network” because this relay process resembles layers of an onion – each relay decrypts one layer of encryption and sends the rest off to the next relay for the next round of decryption. This routing masks both the source and destination locations of the online traffic. This is similar to a VPN in such that you can hide your actual location. The Electronic Freedom Foundation illustrates how the Tor network works with the following illustrations:
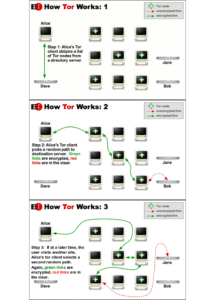
End-users can access the Tor network with the Tor browser. The browser is based on Firefox and comes with the NoScript plugin already installed. You can install the Tor Browser on all major operating systems as well as install the browser on a USB stick or SD card for when you are traveling or won’t have access to your computer.
Tor Considerations
Instead of accessing the internet through a single private network in the case of a VPN, Tor uses a distributed relay network that shifts your “location” every time you connect to the network. Tor is open source and is free to the public, but there are some considerations when choosing to use Tor for online browsing and communications:
- Speed – the Tor network has more users than relays, as well as high user demand, which means slower browsing speeds on Tor than on other networks.
- The Good and Bad of Blocking and Tor
- Bad – some websites block the IP addresses of Tor exit relays (the last server in the relay chain). Those sites will need to be accessed outside of Tor. To add insult to injury, some sites block both Tor AND VPN access, making it near impossible to use those sites without having your location and activity wide open to those sites.
- Good – because of the Tor network’s ability to route traffic through several relays worldwide, Tor can bypass government or other types of geo-blocks on certain websites, making Tor a necessity for those living in areas of the world that restrict access to the web.
- Onion addresses – some websites, on the other hand, have onion addresses that can be accessed through the Tor browser. For example, you can access the BBC News website at https://www.bbcnewsv2vjtpsuy.onion/.
- Anonymity – Tor provides an additional level of anonymity for online communications and browsing with the distributed relay network and browser; however, your actions can still give your location and identity away to third parties. If you log into a service that is connected to your real-world identity through Tor, then the site knows that it’s (most likely) you. Some users use Tor for specific purposes to avoid being identified while on Tor, staying away from logging into services connected to real-world identities. You can use Tor to search online without those searches being tied back to any accounts that are open in other browsers outside of Tor.
Tor @ Your Library
Some libraries include the Tor browser as part of the public computer image, while other libraries allow for patrons to install the Tor browser on the public computer (which then is wiped after the user session). Several libraries also advertise the option to run the Tor browser off of a USB stick to patrons who want to use Tor on public computers.
Several libraries are going beyond offering Tor access to public computers by becoming a relay, increasing the Tor network’s capacity to meet user demand. The Kilton Public Library in New Hampshire was the first public library in the US to host a Tor relay as part of the Library Freedom Project’s Tor Exit Relay Project. The project was not without controversy, but in the end, the public library was allowed to keep the relay.
Tor And Other Privacy Tools And Practices
If you need an anonymous way to browse the internet, Tor is one of your best bets. While some people opt to use both Tor and a VPN at the same time for additional security and privacy, most use one or the other when they need to have a private and secure way to browse and communicate online. Again, each tool has its strengths and weaknesses in protecting your privacy and choosing which one to use depends on your situation. Tor and VPNs are widely known tools, but there are many other tools to cover in our Privacy Tech Toolkit – stay tuned!
Thanks to subscriber Kristin Briney for the topic suggestion!
